
ยินดีต้อนรับท่าน เข้าสู่ เว็บแทงหวยออนไลน์ ที่ดีที่สุด 999LUCKY117 เว็บหวยครบวงจร ต้องที่นี่ที่เดียว !
เว็บหวย999lucky เว็บหวยชั้นนำ ที่มีการบริการดีเลิศรวดเร็วทันใจ ด้วยการการันตี จากลูกค้าหลายๆท่าน เว็บเราจึงเป็นเว็บหวยนึง ที่ลุกค้าหลายๆท่าน ให้ความไว้วางใจด้วย การบริการยาวนานมากว่า 10 ปี !
ยินดีต้อนรับ เข้าสู่ระบบ เว็บแทงหวยออนไลน์ 999LUCKY เว็บแทงหวยออนไลน์ ครบวงจรอันดับ 1 ของคนไทยศุนย์รวมหวยออนไลน์ครบวงจร ครบทุกหวย ที่ต้องการเล่น อธิเช่น หวยเวียดนาม หวยลาว Huayden หวยรัฐบาลไทย หวยมาเลย์ หวยปิงปอง หวยยี่กี หวยหุ้นไทย หวยหุ้นต่างประเทศ และหวยน้องใหม่อย่าง หวยลัคกี้เฮง และ หวยออนไลน์อื่นๆ อีกมากมาย ติดต่อเรา !
แทงหวยออนไลน์2020 กับเรา 999lucky จ่ายไม่ยั้งต้องการมั่งคั่งไม่รู้ตัวอย่ากลัวการแทงหวย ท่านจะได้พบกับ มิติใหม่ ของเว็บ แทงหวยออนไลน์ ที่มีการแทงที่หลากหลาย แปลกใหม่ต่างจากเว็บอื่นๆ ท่านจะได้พบกับ มิติใหม่ของการแทงหวย อย่างนอน !
999LUCKY หวยออนไลน์ ที่มาพร้อมระบบใหม่ ที่ทันสมัย ซื้อง่าย โอนเงินไว จ่ายจริง ได้เงินจริง !
สำหรับ เว็บแทงหวยออนไลน์ ในทุกวันนี้ นั้นมีมากมายจนแถบมองไม่รู้เลยว่า เว็บไหน ที่มีมาตฐาน มีความมั่นคง ปลอดภัย จ่ายจริง ไม่มีประวัติการโกงลูกค้าทางเราจึงขอ แนะนำ เว็บที่คอหวย ให้ความไว้วางใจ 999lucky เว็บแทงหวยออนไลน์ที่มาเเรงที่สุด ในตอนนี้ 2020 มีการบริการที่รวดเร็ว ทันใจมีระบบ ฝาก–ถอน อัตโนมัตที่ทันสมัยเก่าเว็บอื่นๆ อย่างเเน่นอน !
สมัครแทงหวยออนไลน์ กับเราคุณจะได้รับการให้บริการที่เป็นเลิศ เรามีเจ้าหน้าที่คอยให้คำปรึกษาหากเกิดปัญหาใดๆ สามารถติดต่อสอบถามได้ทันที
ข้อดีของหวยออนไลน์ 999lucky
- ระบบ ฝาก-ถอน อัตโนมัติ รวดเร็ว ทันใจ
- รองรับการแทงหวยออนไลน์เต็มรูปแบบ
- ระบบ ติดต่อ ทางทีมงานเราได้ตลอด 24 ชั่วโมง
- ระบบแนะนำสมาชิก จ่ายค่าตอบแทนสูงสุดถึง 5%
- หวยปิงปอง ออกผลด้วยตัวเองได้
- ระบบรักษาความปลอดภัยระดับเทพใช้ Cloud Server เต็มรูปแบบ
- ระบบ สำรองข้อมูลลูกค้าแบบ Ail Time ไม่ต้องกลัวว่าเงินจะหาย ฝาก-ถอน ได้โดยไม่มีขั่นต่ำ
- มีโปรโมชั่นปละสิทธิพิเศษอีกมากมาย
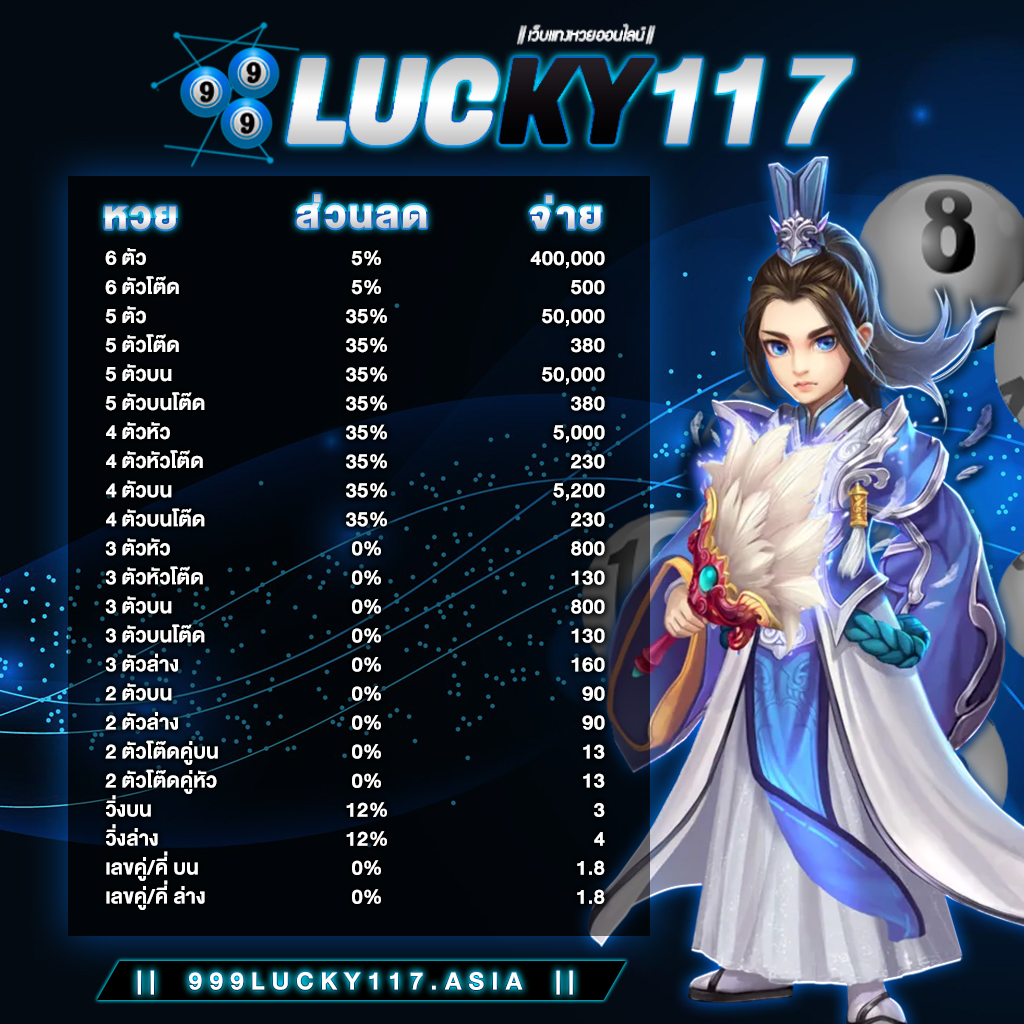
แทงหวยออนไลน์กับ 999LUCKY เว็บหวยที่มาเเรงที่สุดในเมืองไทย 2020
999lucky เว็บแทงหวยออนไลน์ชั้นนำอัดดับ 1 ในเมืองไทย ที่มีผู้คนทั่วโลก และคอหวยทั้งหลาย ให้ความนิยมเป็นอย่างมาก ในขณะนี้ เนื่องจากเว็บมีระบบที่ทันสมัย สะดวก สบายง่ายต่อการใช้งานของลูกค้า และยังมีทีมระดับคุณภาพมืออาชีพไว้คอยดูเเลตอบทุกคำถามทุกปัญหาลูกค้าอยู่ ตลอด 24 ชั่วโมง อีกด้วย ครับ !
แถมทางเว็บเรายังมี กิจกรรม โปรโมชั่น มากมาย เพื่อให้สมาชิกได้เพลิดเพลิน กับทางเราอีกด้วยเพราะฉะนั้น ท่านใดที่ยังมองหา เว็บแทงหวยออนไลน์ อยู่ท่านไม่ควรพลาดเว็บดีๆอย่าง 999lucky ไปนะครับ >>ติดต่อเรา<<
สำหรับทุกท่านที่กำลังมองหา เว็บแทงหวยออนไลน์ ที่ จ่ายจริง ไม่โกงเเละยังมี อัตราจ่ายแพง ที่สุดในตอนนี้ เเละ มีคนไทยนิยม เล่นมากที่สุด 999lucky จึงเป็นอีก 1 เว็บแทงหวยนึง ที่คนไทยหลายๆคน ให้ความไว้วางใจ มากที่สุด !
สมัครแทงหวย999lucky
ทางเข้า999lucky
999LUCKY เว็บแทงหวยชั้นนำอันดับ 1 มาเเรงที่สุดในไทย 2020
มั่นคง ปลอดภัย จ่ายจริง ไม่โกง ระบบ ฝาก-ถอน รวดเร็วทันใจ ต้องที่นี่ที่เดียวเท่านั้น
หวยรัฐบาล | หวยยี่กี | หวยฮานอย | หวยมาเลย์ | หวยออนไลน์

